Information Assurance, Risk and Security in Network Systems

“Measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation.
These measures include providing for restoration of information systems by incorporating protection, detection, and reaction capabilities.”
National Information Assurance (IA) Glossary
What are Information Systems? Systems that store, transmit, and process information.
What is Information Security? The protection of information.
What is Information Systems Security? The protection of systems that store, transmit, and process information.
Information Systems Security
- Information Systems (IS) consists of:
- hardware
- operating system
- application software
- IS Security – a collection of activities that protect the IS and stored data
What is Information Assurance?
- Emphasis on Information SharingEstablishing and controlling trust
Authorization and Authentication (A&A)
What is Cyber Security?
- Protection of information and systems within networks that are connected to the Internet.
Risk
• something bad might happen to an asset
• losing data, losing business
Threat
• an action that could damage an asset
• natural (earthquake, flood)
• human-induced
• businesses need to plan to deal with threats
Threats
• Human-caused threats include:
• viruses
• a program written to cause damage
• malicious code
• a program to cause a specific action to occur
• unauthorized access
Vulnerability
• A weakness that allows a threat to have access to an asset
Tenets of Security: The CIA Triad
• Confidentiality
• Integrity
• Availability
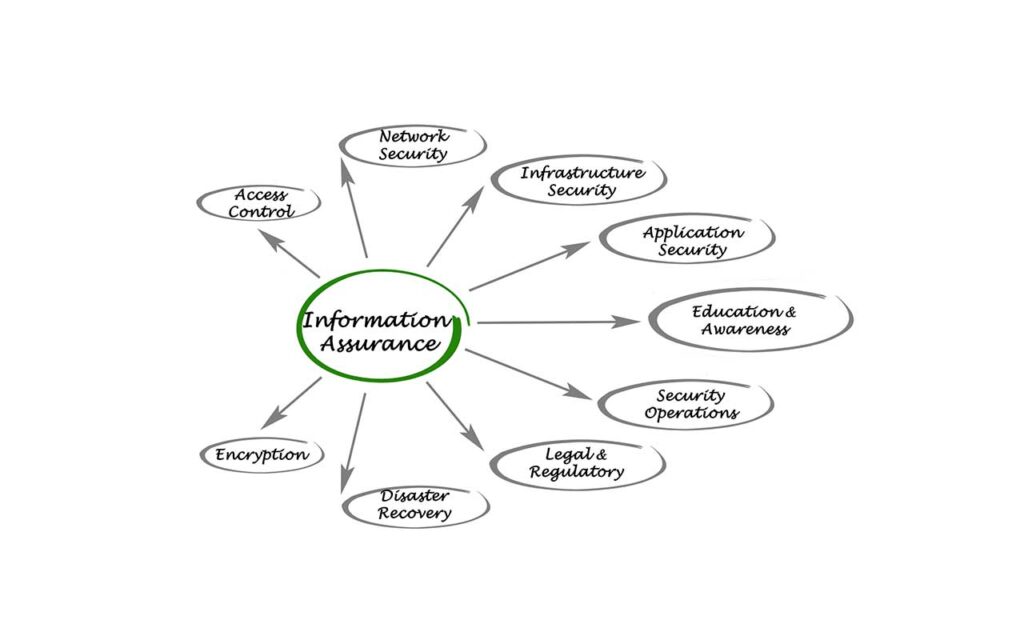
Information Assurance & Security
• Threats: Malware
• Threats: Hacking Tools & Techniques
• Network Security
• Software Security
• Operational Security
• Cryptography
• Access Controls
• Risk, Response & Recovery
Security Mechanisms
▶ Prevention, Detection, Recovery
▶ Prevention:
▶ Encryption
▶ Software Controls (DB access limitations,
operating system process protection)
▶ Enforce policies (frequent password change)
▶ Physical Controls
▶ Detection: Intrusion detection systems (IDS)
Computer Security Operational Model
Protection = Prevention + (Detection + Response)
Prevention Mechanisms
▶ Adequate prevention means that an attack will fail.
▶ unauthorized access e.g. passwords
▶ user cannot override
▶ but, if the password becomes public they will fail
▶ Prevention mechanisms are often cumbersome and do not always work perfectly or fail because they are circumvented.
Detection Mechanisms
▶ Detection is used when an attack cannot be prevented and
▶ it also indicates the effectiveness of prevention measures.
▶ The goal is to determine that an attack is underway or has occurred and report it.
▶ Audit logs are detection mechanisms.
▶ When you log into the design center’s UNIX servers, it gives you the IP address of the last successful login.
Recovery
▶ Recovery has several aspects.
1. stop an attack and repair the damage.
2. trace the evidence back to the attacker and discover the identity of the attacker (this could result in legal retaliation).
3. to determine the vulnerability that was exploited and fix it or devise a way of preventing a future attack.
Example: Private Property
▶ Prevention: locks at doors, window bars, walls round the property
▶ Detection: stolen items are missing, burglar alarms, closed circuit TV
▶ Recovery: call the police, replace stolen items, make an insurance claim …
• Fail Open the mechanism permits all activity
• Fail Closed the mechanism blocks all activity
Principles:
• Different types of failures will have different results
• Both fail open and fail closed are undesirable, but
sometimes one or the other is catastrophic!
Fail Soft
• Fail soft is the process of shutting down non-essential system components therefore
• resources are freed-up to allow essential services to continue operating
Two Factor Authentication
▶ First factor: what user knows
▶ Second factor: what user has
▶ Password token
▶ Passcode creator (every n minutes)
▶ USB key
▶ Digital certificate
▶ Smart card
How a User Should Treat Userids and Passwords
- Like a toothbrush –
- don’t let anyone else use it,
- change it every month or so
- Keep it secret
- Do not share with others
- Do not leave written down where someone else can find it
- Store in an encrypted file or vault
Biometric Authentication
▶ Stronger than userid + password
▶ Stronger than two-facto
Single Sign-On (SSO)
Weakness: intruder can access all participating systems if password compromised
Categories of Controls
▶ Detective controls
▶ Deterrent controls
▶ Preventive controls
▶ Corrective controls
▶ Recovery controls
▶ Compensating controls