MIS Exam Review: Revision Notes for Exam Preparation for Management Information Systems Midterm Exam

This article reviews key concepts and topics to help you excel in your Introduction to Management Information Systems midterm exam.
There are three primary areas that we have covered so far in this course, and they are detailed below. These are:
- An Introduction to Management Information Systems
- An Introduction to Computer Systems: Hardware and Software
- An Introduction to Network Systems and Security
Information Systems
- information
- systems
- decision making
- increased need for information systems
- types of information systems
- enterprise information systems
Computer Systems
- inside a computer
- input and output devices
- system software (operating systems)
- application software (device apps)
Network Systems
- networks
- system protection
- authentication
- access control
- threats – malware
- threats – hacking
Management Information Systems
What is an Information System?
An information system is a set of hardware, software, data, people, and procedures that work together to produce information
- a system
- provides information
- needed by managers
- to support activities
- in achieving business objectives
system
- a system provides information needed by managers to support activities in achieving business objectives system
- a collection of interrelated components that work together towards a collective goal
management information system (MIS)
a system provides information needed by managers to support activities in achieving business objectives
business information system (BIS)
A business information system (BIS) is a group of interrelated components that work collectively to carry out input, processing, output, storage and control actions in order to convert data into information products that can be used to support forecasting, planning, control, coordination, decision making and operational activities in an organization.
Information Value
Right information, in the right form, at the right time, given to the right person
- The value of information lies in its accuracy, relevance, timeliness, and completeness.
- High-quality information supports better strategic and operational decisions, providing a competitive advantage.
- It enables managers to evaluate performance, forecast trends, and identify opportunities.
- Poor-quality information, in contrast, can lead to costly errors and inefficiencies.
See the full information on the Introduction to Information Systems page
Tangible value
- Financial value
Intangible value
- Can’t always calculate value
- Improved decision
- Example : Savings implementing a new system
Good Information
- Accurate correct and verifiable
- Complete yet concise
- Cost effective affordable, beneficial
- Current up-to-date, relevant
- Accessible easy to use
Formal Information
- Consistent, same format, structured
- Accurate, relevant, comprehensive, use templates
- Inflexible, limited, can overlook information
- Ignores opinions, important context
Informal Information
- Flexible, freedom, more details
- Liked by some clients – builds relationships
- Can lack accuracy & relevance, slow & inefficient
- Restricted (can’t deal with large volumes of data)
- Can be ignored, highly selective
Decision Making
Structured decisions
- Rules & constraints known
- Routine
- Re-ordering stock
- Analytical
- can provide justification
Unstructured decisions
- More complex
- Rely on experience, judgement, knowledge
- E.g. open a new branch?
- intuitive
- Based on experience
Decision Levels
Strategic level
Top managers concerned with strategic or long- term planning and decisions
- Unstructured
- Infrequent
- Large impact
- e.g. new market
Tactic level
Middle level managers who make decisions to implement the strategic goals set for the organization
- Medium term planning
- Monitor performance
- Budget & resources
- Set policies – apply to meet strategic goals
- e.g. set department budget
Operational level
Low-level supervisors make daily operational decisions
- Short term, day-to-day control
- Meet the tactical goals
- Highly structured, little impact (organization-wide)
- e.g. daily schedule
Need for Information Systems
The growing complexity of business operations necessitates robust information systems. These systems address critical needs such as automating processes, managing vast data volumes, enhancing customer experience, and improving communication. In a globalized economy, information systems enable scalability, integration across geographies, and real-time analytics to adapt to dynamic market conditions.
The official list of 10 areas (see below) includes the increase in competition such as with globalization, more focus on customers especially with the increased power of social media comments and public pressure, and the speed of change with the uncertainty in the marketplace.
We covered ou thoughts on the increased need for information systems at the beginning of the course. Below is the mind map from that lesson to help remind you of our findings.
- Competition
- Globalization
- Uncertainty in the Marketplace
- Tendency of Outsourcing
- Clout of Civil Society and Media
- Reduced Hierarchy and Improved Transparency
- Focus on Knowledge in Business
- Awareness of the Value from Managing Information
- Customer Focus
- Investment on Information Technology

See the full information on the need for information systems page
Types of Information Systems
Information systems are categorized into various types, each serving a distinct function. Transaction Processing Systems (TPS) handle daily operational tasks, while Management Information Systems (MIS) summarize and analyze data for middle management.
Decision Support Systems (DSS) aid complex decision-making processes, and Executive Information Systems (EIS) provide strategic insights for top-level executives. Knowledge Management Systems (KMS) and Enterprise Systems further streamline processes and improve knowledge sharing.
We will cover the different types of information systems throughout this course. For example, the entrerise systems are covered next.
Enterprise Information Systems
Enterprise Information Systems (EIS) integrate all parts of an organization’s operations. Systems like Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), Supplier Relationship Management (SRM), and Supply Chain Management (SCM) improve coordination, streamline workflows, and enhance decision-making. EIS supports cross-functional integration, real-time information sharing, and scalability in business operations.
It is expected that you understand the basics of these 4 enterprise systems and have a good knowledge of at least one of these systems. Remember we had the lesson that you learnt at least two of the four systems and explained them to other students. It is important that you understand these enterprise systems:
- Enterprise Resource Planning (ERP)
- Customer Relationship Management (CRM)
- Supply Chain Management (SCM)
- Supplier Relationship Management (SRM)
For a comprehensive guide to these systems, and enterprise systems in general, please visit the what are enterprise systems webpage.
Computer Systems
Although computer systems is a wide, complex and important aspect of information systems, in this course we cover the basics of hardware ,software and how computers work.
Hardware: Inside a Computer
The internal hardware of a computer includes critical components such as the CPU, Random Access Memory (RAM), motherboard, and storage drives. The CPU performs calculations and processes instructions, while RAM temporarily holds data for active applications. Storage devices like Hard Disk Drives (HDD) and Solid-State Drives (SSD) retain data persistently.
We studied the inside of a computer and explained the purpose of each of the components on the motherboard. These included:
- motherboard
- CPU
- fan (heat sink)
- memory stick (RAM)
- hard drive storage
- power unit
- communications & input / output (I/O)
- slots / cables
The box that houses all these components is called the system unit. If you want to study more information to prepare for the exam questions then visit the computer hardware page about the system unit.
Hardware Input and Output Devices
We also looked at the range of devices used for input and output to the computer.
System Software
System software, including operating systems (OS) and utility programs, is essential for managing hardware resources and enabling software applications to run. Popular OS examples include Windows, macOS, and Linux. System software also provides critical services like memory management, process scheduling, and file handling, ensuring efficient system operation.
Application Software
Application software is designed to perform specific tasks for users, ranging from productivity tools like word processors and spreadsheets to specialized software for accounting, graphic design, and data analytics. Cloud-based applications and Software as a Service (SaaS) models have revolutionized accessibility and collaboration, enabling users to work from anywhere.
In our lesson we listed the types of software ‘apps’ that are on our devices and listed the actual apps themselves. In the following lesson, we covered system software which includes operating systems and utility programs.
For revision visit the IT software page.
Network Systems and Security
Introduction to Network Systems
Network systems connect multiple computers and devices, enabling data sharing and collaboration. They are classified into Local Area Networks (LAN), Wide Area Networks (WAN), and wireless networks. Network topology, bandwidth, and latency significantly affect performance. Emerging technologies like 5G and edge computing are transforming networking capabilities.
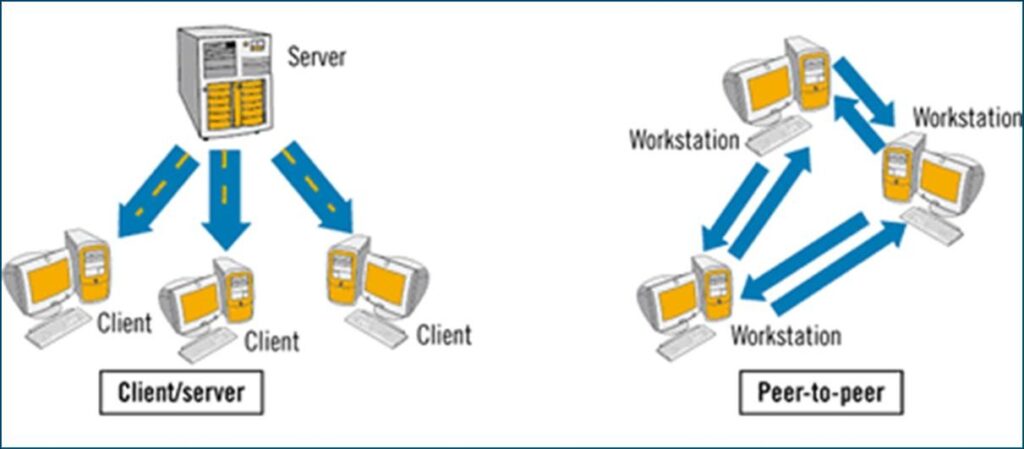
- A group of devices that can communicate with
one another – hosts - Physical connections between devices are called links
- Connections
- Wired – twisted-pair, coaxial cable, or fiber-optic
- Wireless – infrared, microwave (Bluetooth), broadcast (Wi-Fi) or satellite
- Hosts & Nodes
- Host: the central computer that controls the network
- Node: a device that is attached to the network
- Packets
- The format for sending electronic messages
- A fixed-length block of data for transmission
- WAN – Wide Area Network: Covers a wide geographic area, such as a country or the world
- LAN – Local Area Network: Connects computers and devices in a limited geographic area such as an office, building, or group of nearby buildings
- Intranets
- An organization’s private network that uses the infrastructure and standards of the Internet and the web
- Extranets
- Private internets that connect not only internal personnel but also selected suppliers and other strategic parties
- Virtual Private Networks (VPN)
- Private networks that use a public network, usually the Internet, to connect remote sites
Information Assurance and Security
Information assurance ensures the availability, integrity, and confidentiality of data. Security measures such as encryption, authentication, and disaster recovery planning are vital for protecting information assets. Compliance with standards like GDPR and ISO 27001 is essential for maintaining trust and regulatory adherence.
principles : encryption = cryptography
CIA
• confidentiality
• integrity
• availability
in practice:
firewalls and intrusion detection systems
Authentication
Two Factor Authentication
First factor: what user knows
Second factor: what user has
Password token
Passcode creator (every n minutes)
USB key
Digital certificate
Smart card
How a User Should Treat Userids and Passwords –
- Like a toothbrush
- don’t let anyone else use it,
- change it every month or so
- Keep it secret
- Do not share with others
- Do not leave written down where someone else can find it
- Store in an encrypted file or vault
Information Security Threats
Information systems face threats from malware, phishing, ransomware, and denial-of-service (DoS) attacks. Insider threats and human error also pose significant risks. A proactive approach, including regular security updates, employee training, and threat monitoring, is crucial for mitigating these risks.
Risk
• something bad might happen to an asset
• losing data, losing business
Threat
• an action that could damage an asset
• natural (earthquake, flood)
• human-induced
• businesses need to plan to deal with threats
Human-caused threats include:
- viruses – a program written to cause damage
- malicious code – a program to cause a specific action to occur
- Vulnerability – A weakness that allows a threat to have access to an asset
- Security Mechanisms – Prevention, Detection, Recovery
• Viruses: Self-replicating code that attaches to files.
• Worms: Standalone malware that replicates across networks.
• Trojans: Malicious software disguised as legitimate applications.
• Spyware: Software that collects user information without consent.
• Adware: Software that displays unwanted advertisements.
• Ransomware: Malware that encrypts files and demands payment for decryption.
• Rootkits (Backdoors)
Information Systems Access Control
Access control restricts unauthorized access to systems and data. Methods include authentication (passwords, biometrics) and authorization protocols (role-based access control). Advanced measures like multi-factor authentication (MFA) and identity management systems further enhance security. Proper access control reduces data breaches and ensures system integrity.
User – Any person accessing a computer system
Group – Multiple users that are granted access to a resource at the same time Role – Access is granted or denied based on a person’s job or function within the
organization
Final Exam Review
The final exam will focus on the subjects after midterm that include data systems and databases, business processes and a closer look at information systems. The mis final exam will be based solely on this material after the midterm exam.